Defense in depth
Defense in depth
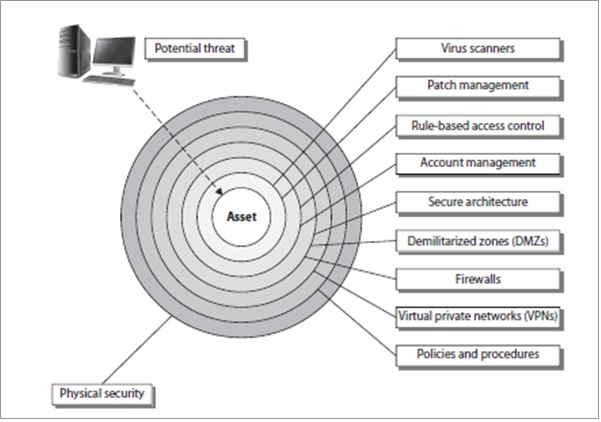
This one is what we try to accomplish in security. Meaning we try to have different layers of security interconnected because as we know by fact no security control is unbreakable. In this strategy even if an attacker can bypass some defense layers it is almost impossible to bypass them all without us getting alerted and being prepared.
There are three main types of controls:As you can see in the first one, we have a logical control, something we apply using the system logic. The second one is using a procedure making not allowed, meaning electrician can enter the data center, but not without breaking the procedure. The third one is easier to understand as it offers limitation using physical controls like locks, keys or in this case the elevator to access a restricted area.